In this article, we will look how to Action-Based Extendibility (ABX) action to fetch Gitlab or Github SSH Keys and use them in a VMware Cloud Assembly Blueprint Deployment.
Introduction
When building Cloud Assembly blueprints there are multiple methods that you can specify what type of remote access would be possible to the machine after it has bene provisioned. You can set these via the remoteAccess property in your blueprint YAML code.
One of the popular ways is to use publicPrivateKey as a remoteAccess authentication method and supply the SSH Key in the YAML.
my-vm:
type: Cloud.Machine
properties:
remoteAccess:
authentication: publicPrivateKey
sshKey: SSH KEY GOES HERELets see how we can dynamically supply this key during poisoning time.
Issue & Solution
Problem with the above approach is that you have to preconfigure the ssh key value in every yaml blueprint you manage. What if we want to pull the ssh key value from a git repository like Gitlab or Github or any other URL for that matter.
We cannot dynamically specify the value in the YAML but we can build an Action-Based Extensibility (ABX) action to fetch the value and inject it the YAML during provisioning.
Action-Based Extensibility uses streamlined scripts of code within Cloud Assembly to automate extensibility actions.
Action-Based Extensibility provides a lightweight and flexible run-time engine interface where you can define small scriptable actions and configure them to initiate on particular events provided by the Event Broker Service (EBS).
You can create these extensibility action scripts of code within Cloud Assembly and assign them to subscriptions. Similarly to workflows, the extensibility action script triggers when a event specified by a subscription occurs. Extensibility action scripts are used for more lightweight and simple automation of tasks and steps. They are also hosted on the cloud as opposed workflows which are hosted on-prem using a vRealize Orchestrator client and server.
Lets see how we can do this.
First lest specify the remote access method in our blueprint yaml and give a null value for the ssh key:
my-vm:
type: Cloud.Machine
properties:
remoteAccess:
authentication: publicPrivateKey
sshKey: nullNavigate to the Extensibility tab in Cloud Assembly.
Navigate to Actions and click New Action
Provide the following value:
- Name: Give it a name
- Project: Attach it to your project that contains your blueprint yaml.
- Template: custom script
- Runtime: python 3
Copy and paste the following script in the script filed:
import requests
def handler(context, inputs):
# Modify the URL to point to your Gitlab, Github or any other URL that holds the ssh key
response = requests.get('https://github.com/KaloferovLab.keys')
# Set encodding to UTF-8
response.encoding = 'utf-8'
# Remove new line breaks from the text
ssh_key = response.text.replace("\n","")
print(ssh_key)
# Read the sshKey value from the Properties section fo the blueprint payload
old_key = inputs["customProperties"]["sshKey"]
new_key = ssh_key
# Create outputs and assing new key valye
outputs = {}
outputs["customProperties"] = inputs["customProperties"]
outputs["customProperties"]["sshKey"] = new_key
print("Setting machine sshKey value from {0} to {1}".format(old_key, new_key))
return outputs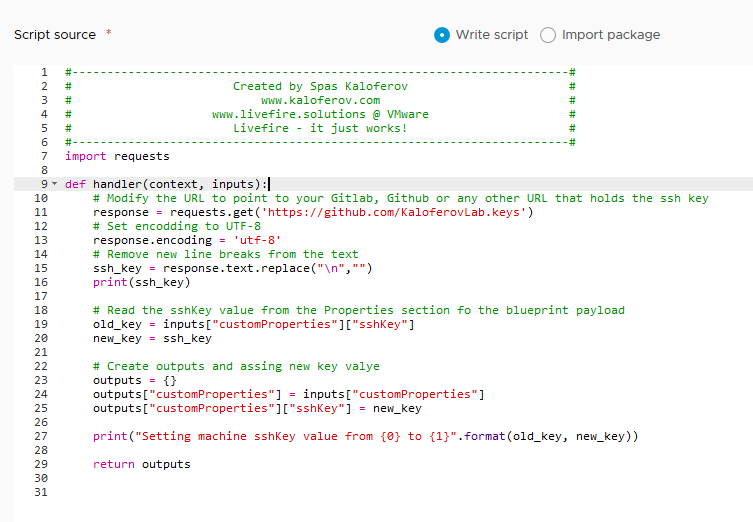
Replace the response URL with the URL holing your ssh key.
On the right side provide the fallowing values:
- Main function: handler
- Inputs: customProperties : [“sshKey”]
- Dependency: requests

Save the action.
Go to the Subscriptions tab and create a new Subscription.
Provide the following values:
- Name: give it a name
- Event Topic: compute.allocaiton.pre
- Runnable Item: the action you created
- Blocking: Enable

Save the subscription.
Trigger a deployment of the blueprint
Monitor the action run and wait until it has completed.

Now you should be able to login via SSH to the machine you’ve just deployed.





