My dear NSX Ninja, this is my first post on this blog and it is a part of the Troubleshooting (TRBL) and Commands (CLI) series. In this series, I will show you a couple of interesting topics about TRBL and CLI which can help you with NSX each day.
We have the following packet capture commands:
pktcap-uw and tcpdump-uw commands are native to ESXi hostsstart capture command is the NSX packet capture tool, I will cover this in part 2 of this post.
First, we will look at packet capturing CLI pktcap-uw which we can use for capturing and TRBL on ESXi host.
esxcli,net-stats, and esxtop Commands
Before we start using pktcap-uw we need to gather a couple of information for packet capturing. We can use different CLI on the ESXi host. I will show you CLI which you can use.
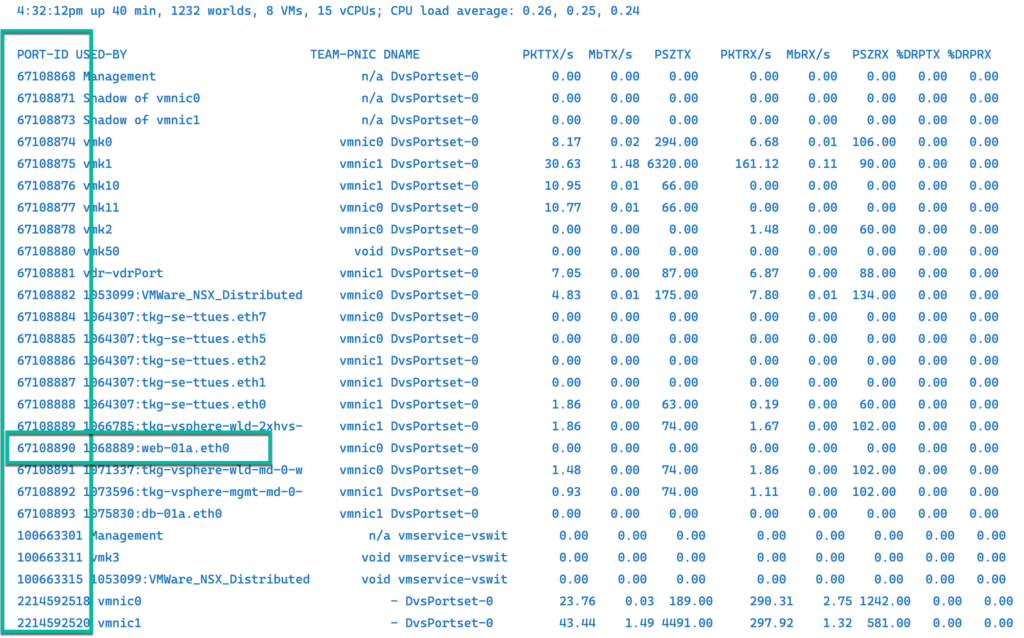
ESXTOP
Esxtop utility by default run in interactive mode and if you want to see the Network panel you need to type the letter n as an n:network
We need to know PORT-ID for web-01a VM.
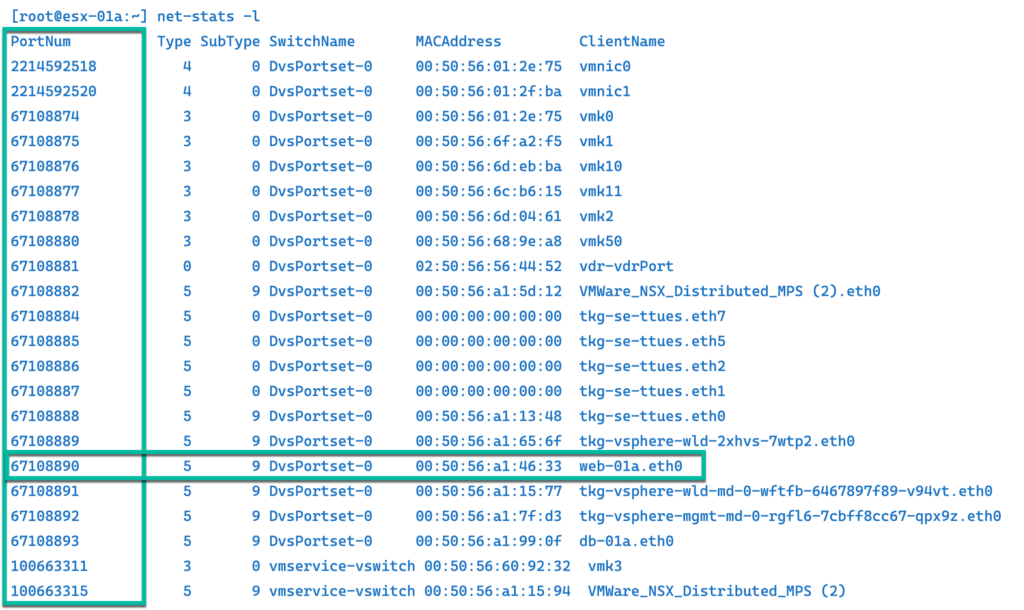
NET-STATS
This command net-stats is very powerful and can get you a lot of deep-dive information. In my example, I use for the same information as esxtop utility so you can choose which command is better for you. net-stats -l list ports in the system.
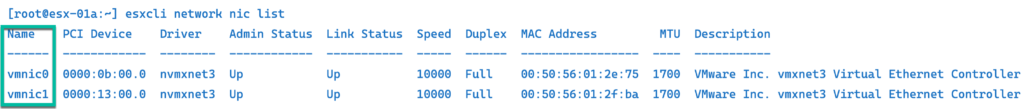
ESXCLI
You can use esxcli command to manage many aspects of an ESXi host. In our case, we just use to list all Physical NICs loaded on the system.
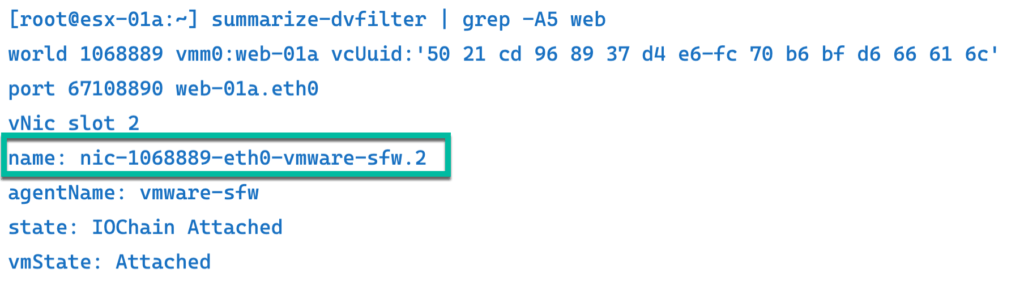
SUMMARIZE-DVFILTER
We use summarize-dvfilter command to get the vNIC filter for the web-01a VM. We can see the filter name for slot 2 attached.
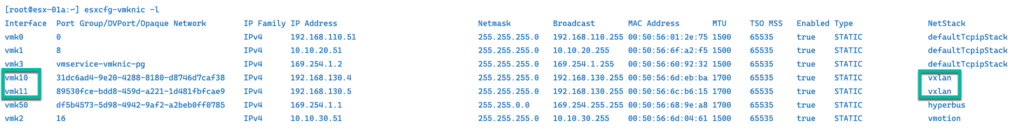
ESXCFG-VMKNIC
There is also another CLI little bit older but still valid. esxcfg-vmknic -l commands we use for listing VMkernel NICs. ( Yes you can use esxcli but this is just an example of another command )
pktcap-uw Command
At this moment we gathered all information that we need for packet capture with pktcap-uw command.
Note: Certain options of the pktcap-uw utility are designed for VMware internal use only and you should use them only under the supervision of VMware Technical Support. These options are not described in the vSphere Networking guide.
https://docs.vmware.com/en/VMware-vSphere/8.0/vsphere-networking/GUID-30003897-2101-459C-81FA-FCB42313237E.html
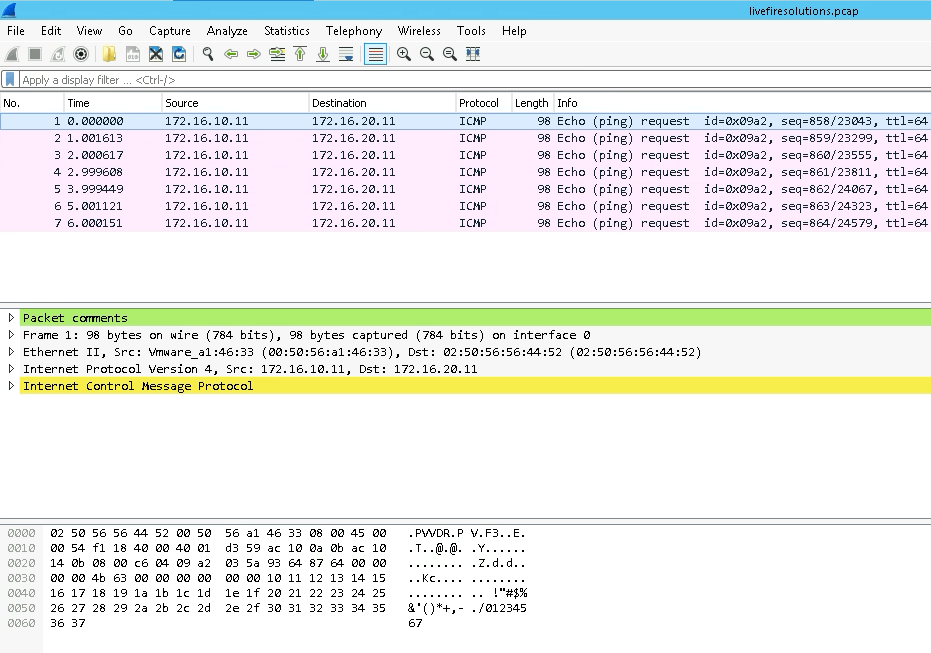
For example I ping from web-01a IP 172.16.10.11 to the db-01a IP 172.16.20.11
We can use the pktcap-uw command to capture packets from the ESXi host and analyze the output with the tcpdump-uw command. pktcap-uw has a lot of options. I will describe the important ones for you. The first is the –dir option to capture the packet according to the direction. ( By default captures the incoming traffic ) The second is -the-stage option to capture the traffic before or after the dvfilter.
–dir 0 – capture incoming traffic
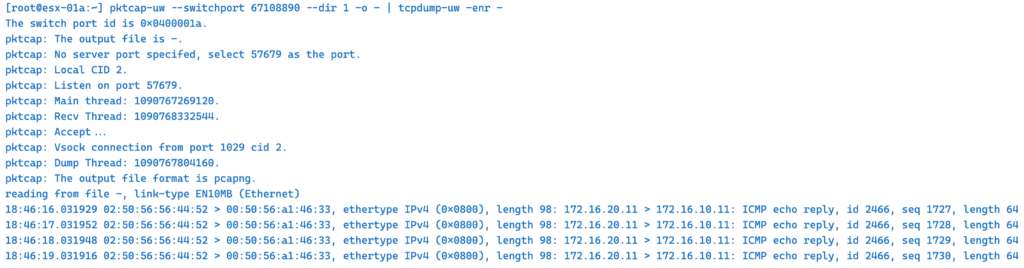
–dir 1 – capture outgoing traffic
–dir 2 – capture both traffic
The direction of flow, with respect to the vswitch:
0- Input: to vswitch (Default), 1- Output: from vswitch, 2- Input and Output
–stage 0 – before traffic dvfilter
–stage 1 – after traffic dvfilter
Following example shows we are capturing packet for a port web-01a VM and the port number is associated with web-01a.eth0 interface. Only incoming packets are captured and saved in file named livefiresolutions.pcap.

In the following example, we capture the physical NIC vmnic1 on host esx-01a and redirect the output to tcpdump-uw Immediately.
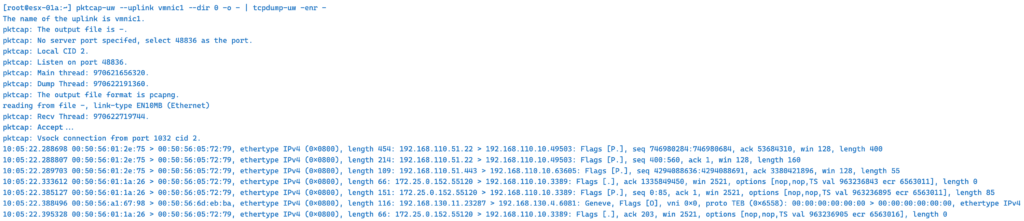
In the following example, we capture VMkernel port vmk10 ( TEP ) –dir 2 both Input and Output.

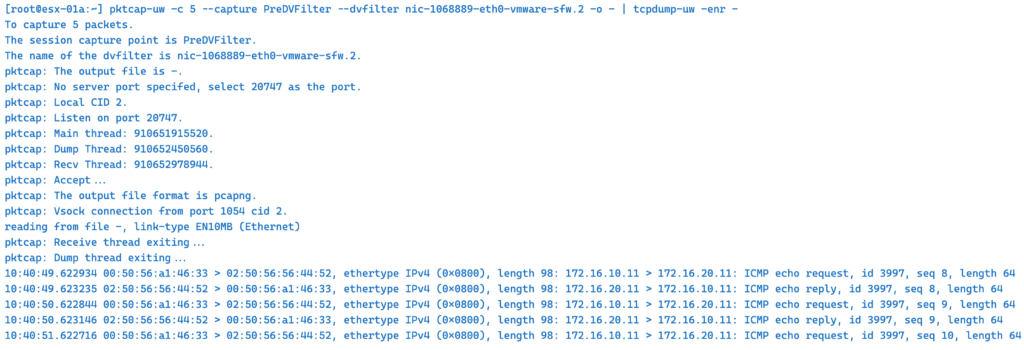
In the following example we capture dvfilter web-01a VM – PreDVFilter — Before DVFIlter capture point
This is my last example for pktcap-uw with –trace option captures each packet at each point and is very verbose.
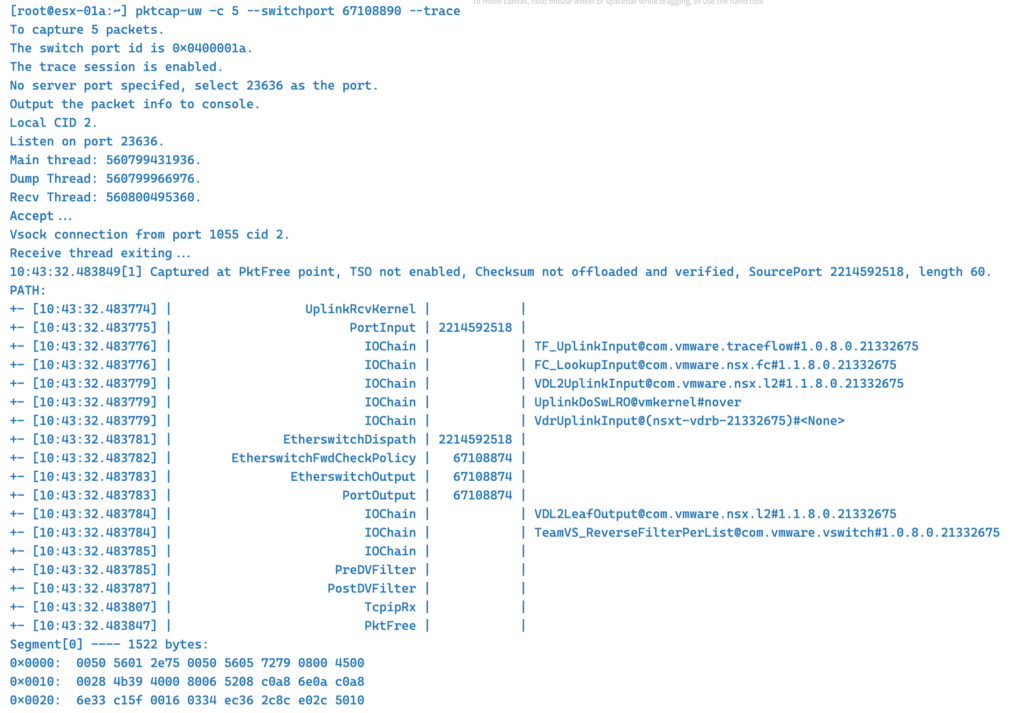
tcpdump-uw Command
The last command is tcpdump-uw it can capture vmk , but not in switch ports or uplinks. I used it here only to decode pcaps online or read them.
We use tcpdump-uw to read our previous file livefiresolutions.pcap
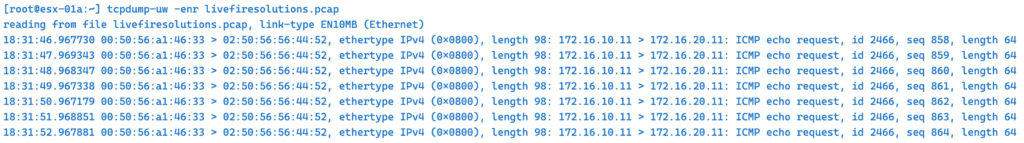
Or we can decode pcap online
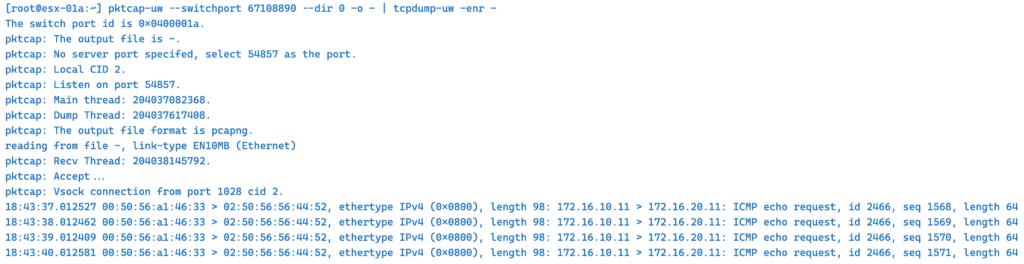
The same example only we change –dir
Of course, if you prefer to read .pcap in Wireshark you can copy the file to your local desktop.
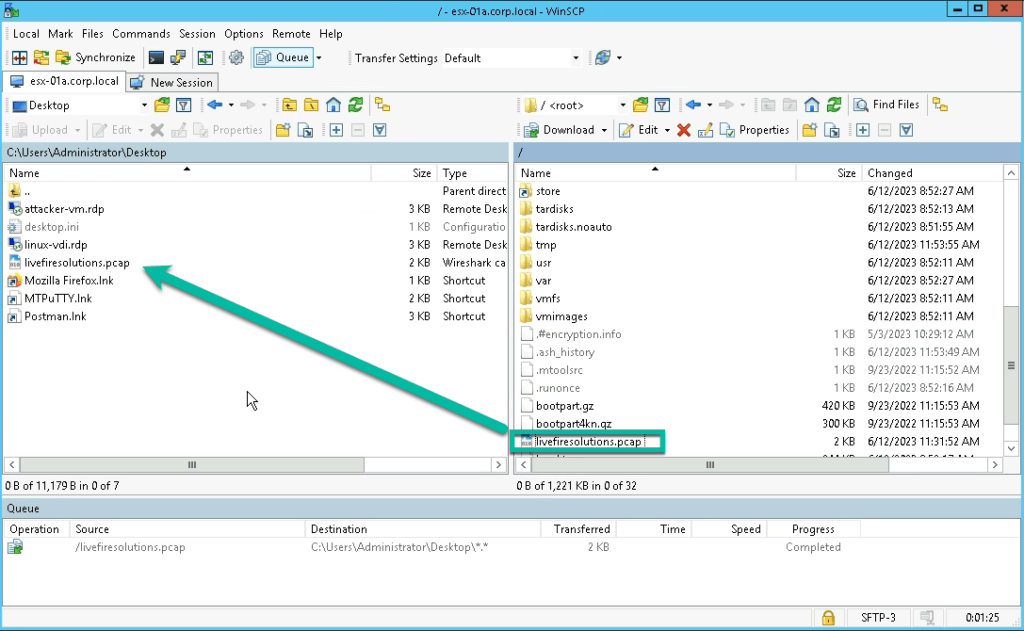
Open with Wireshark
I hope these short examples will help you with small TRBL in your environment. Enjoy packet capturing and See with another post.
Self-study source for you:
esxcli – https://developer.vmware.com/web/tool/7.0/esxcli
pktcap-uw – https://docs.vmware.com/en/VMware-vSphere/8.0/vsphere-networking/GUID-5CE50870-81A9-457E-BE56-C3FCEEF3D0D5.html
vsphere-cli – https://developer.vmware.com/web/tool/6.7/vsphere-cli