All the profiles in NSX-T can be quite confusing at the beginning. In this article I want to take a look on the most important ones and how they relate to each other.
- In which profile do I have to define the Transport VLAN?
- Where do I map the physical adapters in my host to the uplink definitions?
- Where does this N-VDS comes from?
- … and so on.
Questions like the ones above might come up now and then when you start working with NSX-T. To setup up a working virtual network infrastructure it is crucial to understand these profiles, where they are used and how they interact. So let’s take a closer look on the profiles in NSX-T 2.4.
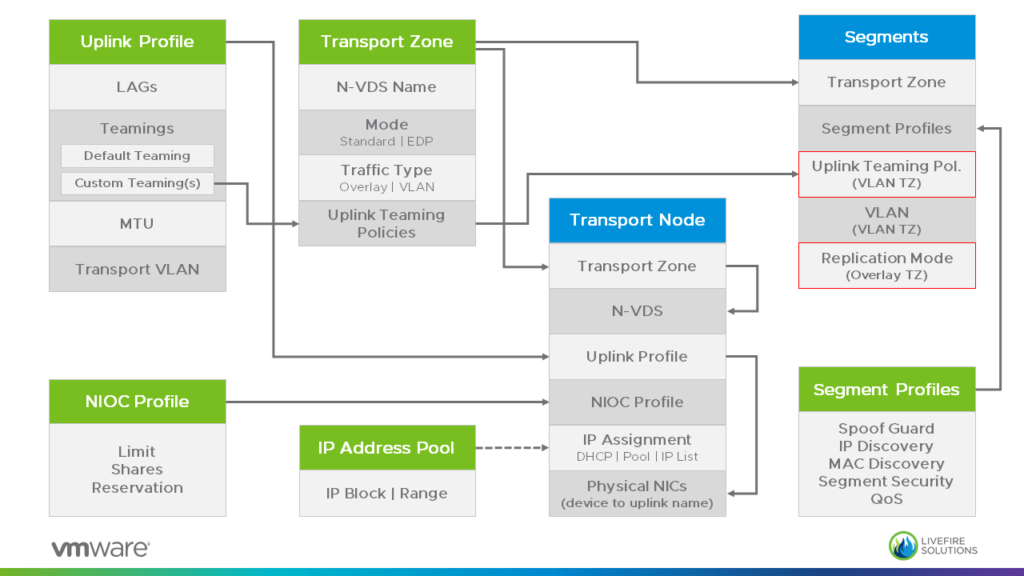
The diagram above shows:
- Profiles and other logical items are marked with a green header
- Datapath items have a blue one.
- Transport Node refers to a single Node, but the same settings are configured in a Transport Node Profile which can be attached to a vSphere Cluster.
- The red-framed items for Segments are accessible via Advanced Settings.
Note: We will discuss Transport Node Profiles in one of the upcoming posts.
Now lets talk through some of the highlights:
Transport Zone
This is one of the first objects you have to create: You select its type (VLAN or Overlay) and define an N-VDS. When you then assign a Transport Node to the Transport Zone it automatically inherits the N-VDS defined in the TZ. Please note the arrow at the Transport Node going from the Transport Zone to the N-VDS.
Uplink Profile
Although NSX-T comes with some pre-defined Uplink Profiles I would recommend to create your own ones. This type of profile basically defines all the aspects on how to attach a Transport Node (ESXi, KVM, Edge) to the network: It defines the Transport VLAN, MTU size and the NIC configuration.
I like to see the Transport Node setup split up into 4 layers:
- You create a Transport Zone and
- define its N-VDS name.
- Then you use the Uplink Profile
- to attach your Transport Node to this construct.
Segments and Segment Profiles
Segments (aka Logical Switches) always belong to one Transport Zone. Depending on the type of TZ you can configure different options like Replication Mode for Overlay based Segments or Teaming Policies for VLAN Segments.
Note: We will cover Teaming Policies in an upcoming article.
NSX-T comes with a lot of Segment Profiles out of the box and most of them will work for the majority of use cases. Nevertheless following a (very short) summary:
- Spoof Guard: Enable/disable Port Bindings basedon IP/MAC
- IP Discovery: Configure ARP and/or DHCP snooping, etc.
- MAC Discovery: Setup MAC Change and MAC Learning rules
- Segment Security: BPDU and DHCP Filter, Rate Limits, etc.
- QoS: DSCP (trusted or untrusted), CoS, Bandwidth limitations
These profiles are attached at the Segment level but can be overwritten on the Segment Port level.
Whats Next…
In the upcoming posts I want to talk about:
- VLAN traffic pinning using Teaming Policies
- VMkernal Adapter management using Transport Node Profiles
