I have a kubeconf file, but I cannot find the key and the certificate that was used to create it. Here comes help…
kubeadm does a great job in creating all the necessary keys, certificates and kubeconf files required for a Kubernetes cluster. As I was playing around recently with users, roles, and kubeconfs I discovered that the key and the certificate for the kubernetes-admin are missing.
And here I want to demonstrate how those files can be exported from the kubeconf.
In one of my previous posts I talked about how to create a user, its permissions and roles in Kubernetes:
https://www.livefire.solutions/kubernetes/create-a-user-in-kubernetes
Take a look if you want to learn more about how these kubeconf files are created.
Starting Point
I have setup my Kubernetes cluster using kubeadm and per default kubeadm stores all the certificates and keys in the /etc/kubernetes/pki directory. But as we can see below there is no admin.key and no admin.crt file:
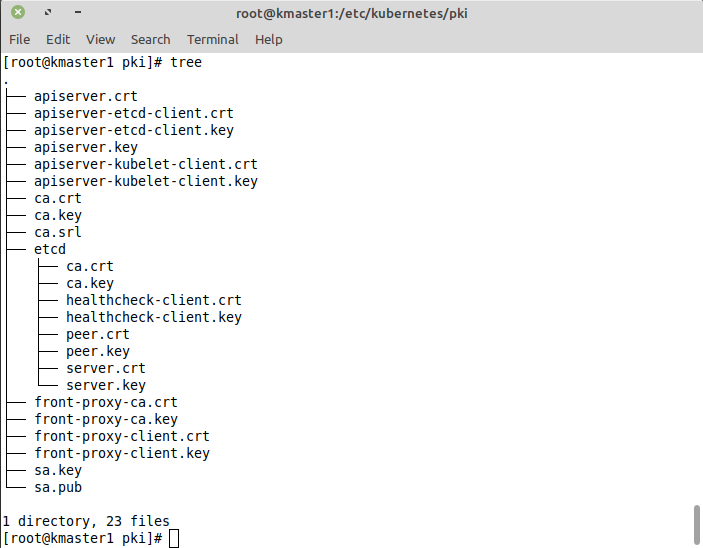
So lets export them from our admin kubeconf file stored in /etc/kubernetes
Verify Content and Export Certificates
Lets take a view on the content of: /etc/kubernetes/admin-conf
Note: To preserve readability lines are cut off.
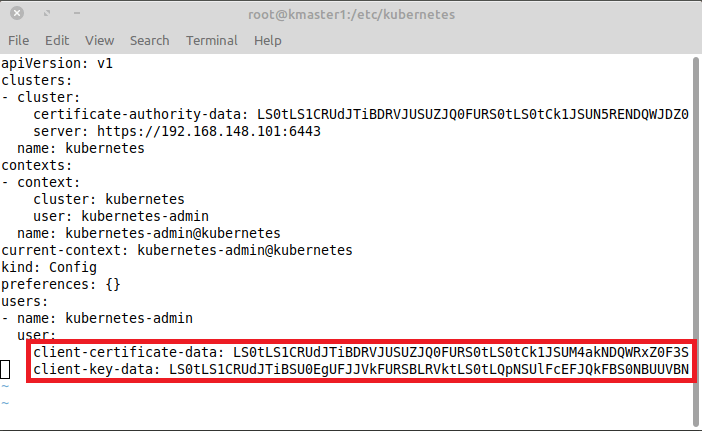
We are interested in the two lines at the end that contain the key and certificates information. So lets grep out the client-certificate-data and decode the content:
grep "client-certificate-data" admin.conf | awk '{print $2}' | base64 -d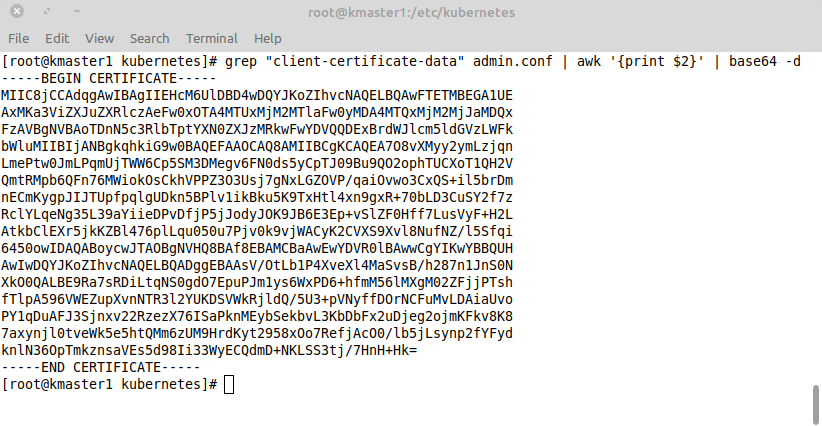
As you can see above, the result looks very familiar… 🙂
Repeat the step for client-key-data and write the output to files:
grep "client-certificate-data" admin.conf | awk '{print $2}' | base64 -d > admin.crt
grep "client-key-data" admin.conf | awk '{print $2}' | base64 -d > admin.keyIn a final step, lets verify the exported admin.crt
Show the first 20 lines of the certificate information by running:
openssl x509 -in admin.crt -noout -text | head -20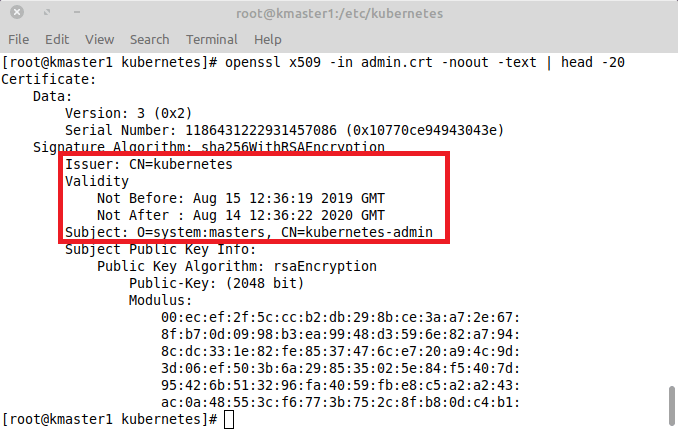
We can see the issuer, validity and subject information. Seems our export was successful.
