When one launches the Horizon HTML client using the Blast protocol the experience for me in our lab environment was never straightforward. The Browser constantly got stuck even though our Connection server had trusted CA signed certificates from a public source. Recently we were on partner site and the partner explained how a customer was dissatisfied with the hiccup. We had to find a solution to this integration problem.
The problem would only occur if we were using HTML blast via VMware Identity Manager.
Let’s describe the problem more closely. After launch the FQDN would redirect to an IP Address and then the user would have to accept and click again to move on. Not so smooth

When investigating and doing research, it was suggested to me to try this article on the VMware docs site and I gave it a go.
https://docs.vmware.com/en/VMware-Horizon-7/7.5/horizon-installation/GUID-8E7FBB9D-F2DB-4787-B11B-7506126DEB7F.html
It requires that one goes to adsiedit.msc on the horizon broker and change the preferDNS under CN=Common in the Horizon LDS database
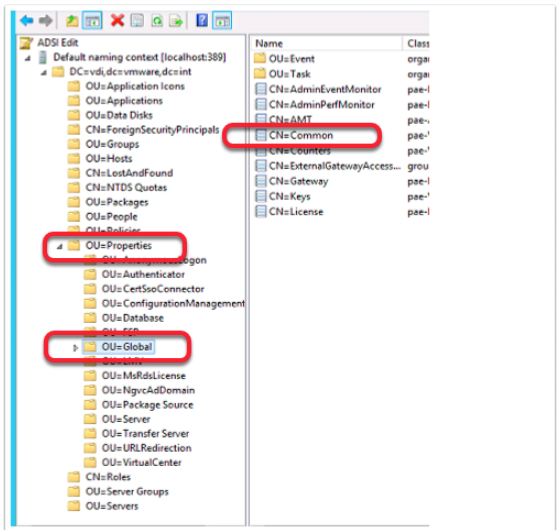
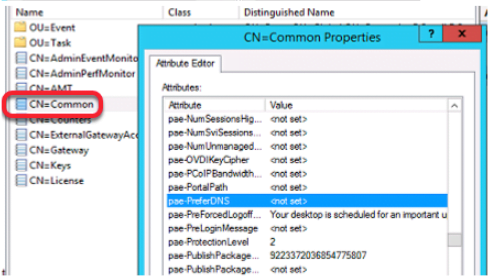
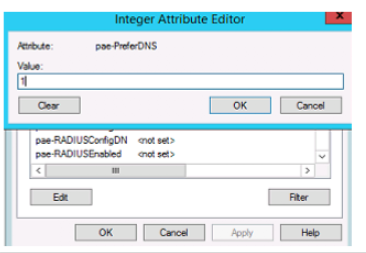
After this, I tested the session again and this is what I noticed. The settings worked, the IP address was no longer there, but I still had the problem.

After further research, we found the following VMware knowledge base article: When connecting to a Horizon view virtual machine using Blast, SSL Session is invalid (2088354)
- It suggested replacing the default Blast certificate on the Parent image with a CA-signed certificate
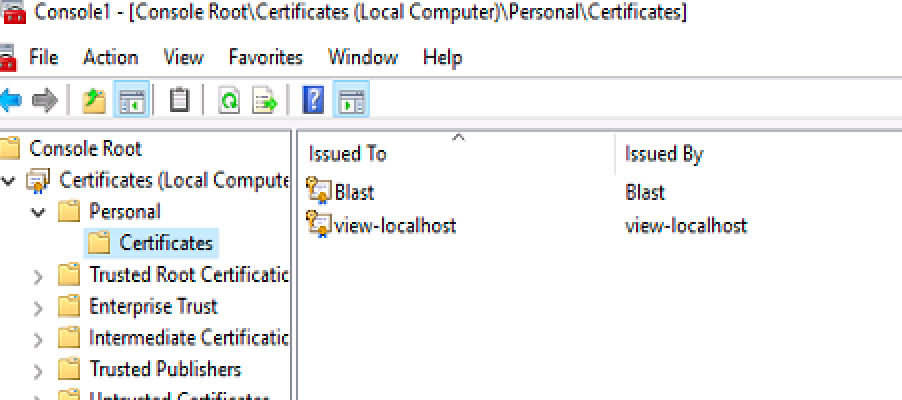
- OLD default Blast

- New
- It has to be a CA-signed certificate along with its chain when importing it has to be marked as exportable and imported with extended properties.
The next thing I had to do was set the certificate thumbprint in the registry
- I opened regedit.exe on the Master virtual machine and followed the below registry path:-HKEY_LOCAL_MACHINE\SOFTWARE\VMware, Inc.\VMware Blast\Config registry key.
- I had to go to the certificate properties, copy the thumbprint and save it in Notepad. After pasting the thumbprint, I had to leave a space after every two characters except on the last character.
- I then opened the SslHash key and replaced the existing thumbprint with the new certificate thumbprint.
The knowledge base in the very last line makes this statement
Update the View Agent ADM Template Settings for the Agent VMs
Enable the Connect using DNS Name GPO configuration setting.
- I imported the Horizon 7.5 GPO settings into the Master image and saved the .xml files into the local policydefinitions folder. What I discovered is the GPO setting no longer exists in the Template.
- My understanding at present is this is now configured in the LDS database on the Broker. (discussed right at the start of this blog)
I went back and tested a Workspace ONE client session through web portal and a Workspace ONE windows 10 Application


The User Experience was awesome, seamless single-sign on with no hiccups. It worked!
In Summary, both the certificate replacement on the client agent side and the adsiedit configuration are required on the Broker for this to work.
We now have this as one of our Hands On labs in our EUC-Livefire Digital Workspace offering which is available to internal PSO and SE’s and VMware Partners Globally.



Hello,
thanks for this clear post.
I’m trying to sort out the same situation here (Horizon 7.4) but when in the last step I restart the VMware Blast service, the Sslhash thumbprint gets regenerated and it is not keeping the thumbprint of the CA-signed certificate. Thus, I always get the same certificate message when connecting to the vdi desktop.
Is there something that you have faced as well?
Or did your thumprint of the sslhash value remained after the Vmware blast service restart?
What were the purposesof your CA-signed certificate? I have only server authentication and client authentication. maybe more purposes are needed for this Blast connection?
Thanks
Oriol
Hey,
I like your post which i followed until , now i am stuck with the RDS server presenting its server name instead of the name on the certificate.
can you assist?
Hi
Please email us at [email protected]
We can possibly look at ways to helping you.
Thanks